Last week I presented at an event for schools, speaking in relation to AI in education. As such I thought I would share the main points from my session. Now the session itself was broken into three main sections, being some context, the short term implications and the implications beyond the short term.
Context
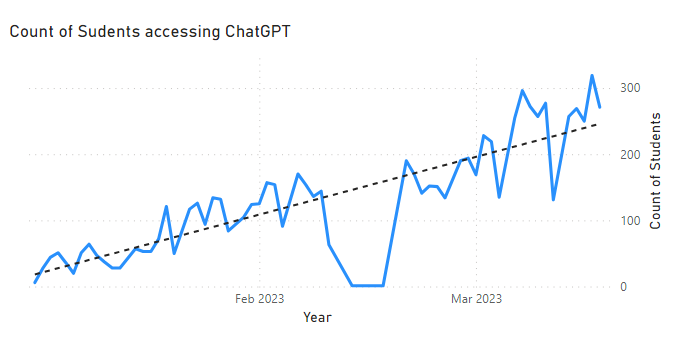
The first point I made was on the current post ChatGPT discussion in relation to AI, and how AI itself isnt new. In fact solutions we use in everyday life, such as Siri and Alexa, such as Google Maps and search and facial recognition all make use of AI. Although generative AI began to be so easily accessible in ChatGPT in November of 2022, AI had been around for quite a while prior to this and had already formed a big part of our lives. I also acknowledged that independent of whether schools do anything in relation to generative AI, including ChatGPT, our students will largely already be using these solutions; An examination of internet traffic in my own school saw an increase in student daily use between Jan and March 2023, at which point we stopped tracking the data as generative AI started to appear in many different solutions. And this is a key point, that if schools do nothing, and leave the use of AI solutions to chance, both in the hands of their teachers and their students, AI solutions will be used whether this is appropriate, safe or not.

In looking more broadly at AI, I would suggest that it represents a continuum between extremes of narrow AI solutions, which are capable of a single activity, up to the holy grail which is AGI (Artificial general intelligence) where the AI solution is capable of the broad spectrum of human activities. Where we are currently is heavily down the left hand, and narrow AI side of things and I suspect we will be there for a while. Looking at the responses of 350 AI experts in relation to when there will be a 50% chance of an AGI existing, 50% said this would occur in the next 40yrs however to increase the confidence to 90% of experts, you need to look out to 100 years time. There is little consistency in the responses other that almost all of the experts predicted AGI would occur at some point in the future.
The short term?
Coming back to the present day and the challenges of generative AI, it is also important to acknowledge the challenges in education more generally. A 2022 Teacher Wellbeing Index showed 59% had considered leaving the education sector during the year due to mental health and wellbeing pressures while 68% said volume of workload was an issue making them consider leaving the profession. And it is here that maybe AI can start to help in addressing some of the workload issues, and through this hopefully reducing stress and pressures on mental health. Through the use of AI, administrative burdens such as policy and resource creation, marking, parental reports, meeting minutes and reading of minutes, and many other takes can be lightened. Now in all cases there still needs to be a human element to review, amend and improve AI generated content, but through humans working with AI tools we should be able to accomplish things quicker and easier.

And generative AI isnt limited to the boring and administrative tasks, but can also help with the creative tasks, which in my case, I am not particularly strong at. Being a poet, artist, musician, videographer and similar has never been my strong suit however with AI I can create things which previously may not have been possible. Having asked ChatGPT for a poem on the impact of AI on education, for example, I was impressed by the output.
So what are schools to do?
I think the first thing is to acknowledge that AI comes with risks and benefits and that you cannot have one without the other. As such the first thing a school needs to do is have a discussion and establish what their risk appetite is. Does the school want to make the most of all the benefits of AI, and therefore is willing to accept some degree of risk, or is the school risk averse and therefore not willing to risk making use of AI? Once risk appetite has been established it is now possible to set some ground rules an guidance for staff and students and this is where schools need to put an appropriate policy in place in relation to AI use. This policy should cover things such as the legal implications, such as GDPR and data protection related, the ethical considerations and also how risks and benefits need to be considered. Equally any policy in relation to AI needs to be aligned with the wider school values and vision, plus needs to be regularly reviewed and updated. Now that a policy is in place, the next step is to speak to students and staff about AI, about the risks and benefits and about the policy requirements. Once basic awareness is in place, you can then begin exploring and experimenting with AI solutions including the many generative AI solutions which are now so freely available.
Beyond the short term
Moving beyond the now and the short term where we can clearly establish some steps which schools should be taking, we move into the more unpredictable future, where the questions are more questions for education in general, rather than things schools can easily individually action.
One of the first challenges or questions relates to originality and we are already seeing this in the actors strikes and in a number of copyright actions being taken against Generative AI vendors. What does it mean to be original in the world of ready access to generative AI? The JCQ guidance for example states that “All coursework submitted must be the candidates own work” but does that mean a student cant used generative AI to help or as a starting point, or a dyslexic student cant get the help of generative AI? And to complicate matters even further, consider what being original might mean in the time of the romans; Basically you couldn’t write or say the same as someone else, but at that time there were less people in the world and little was written down for comparison. Now we live in a world with more people, writing more often and in more forms than ever before and that’s even before we consider how people might now use generative AI to create yet more content, much quicker than they did before. So what chance do you we have in being original or presenting our “own” work? This is a big challenge for education, especially given our current system uses coursework as an easy proxy for learning.

We also need to consider how the fundamental process of education, with students going to schools, colleges and universities may need to change. A perfect example is how students unable to study calculus at school can now meet the requirements of CalTech in relation to calculus through the use of 2 online platforms. Basically, students can prove their master online rather than in a school, then progress onwards to CalTech. It is likely therefore that new avenues of education progression, access to education and whole new programmes may appear as we move forward, but how will this impact the schools and colleges we have today; It may be in the future that they look significantly different to how they look today.
And the third of my future gazing thoughts, and the most significant in my eyes, is the access to online AI based tutoring for students. This potentially provides every student with 1:1 access to support for their learning rather than the division of a teachers time across the whole class. Additionally, this support is available 24/7/365. This will likely impact on the core subjects at basic learning levels initially so basic maths, English and science in the first instance before broadening out to other subjects. It may be this online personalised education which has the biggest impact, freeing up teachers to focus on some of the areas which have long needed time in the curriculum, but long gone without; mental health, resilience, digital citizenship among other areas. It will allow teachers to spend more time on the things which matter most about being human, having had time freed up by AI in relation to the things an AI can do reliably well.
Conclusion
AI is here now so all schools need to act as staff and students will use the available tools as they see fit if they do not receive any training or guidelines from the school. As such all schools, in my view, should have a policy on AI use within the school as a minimum. In terms of the potential of AI as is now available, I referenced my own use of Canva, ChatGPT, MidJourney and DallE-2 in the creation of my presentation and presentation content.
Looking out beyond the short term, things are not quite as certain with more questions than answers. One thing I think we can be reasonably sure of is that AI’s impact on education will only increase and it may lead to some fundamental questioning of our current educational system and approaches to education. And at some point in the future the singularity, where AI intelligence exceeds that of humans, will likely be reached and at that point I suspect the world, and education, may look very different to today.